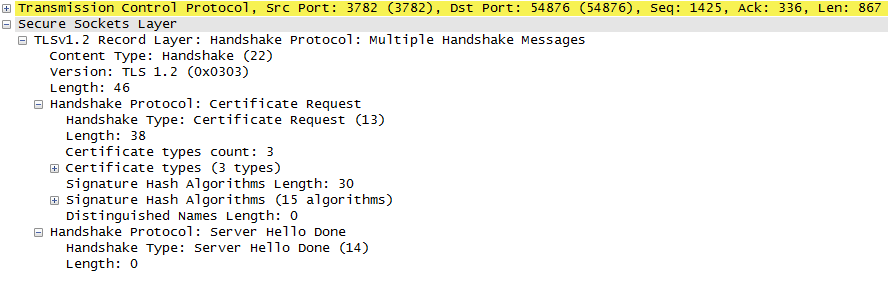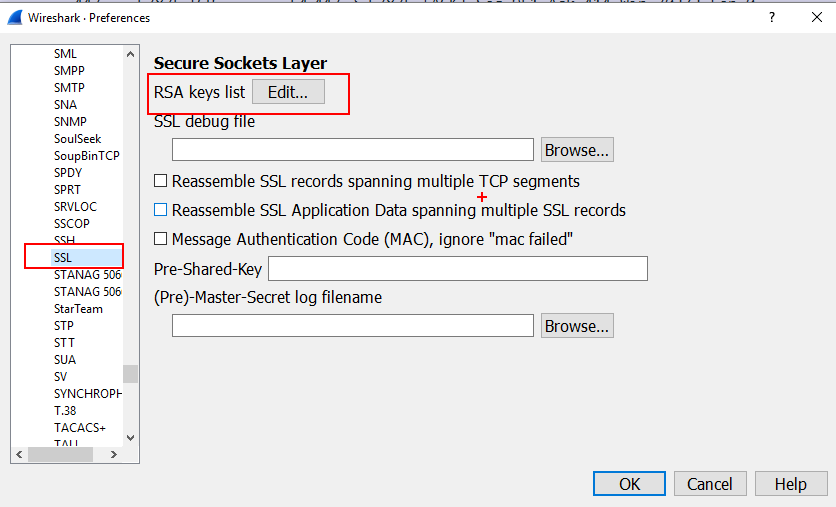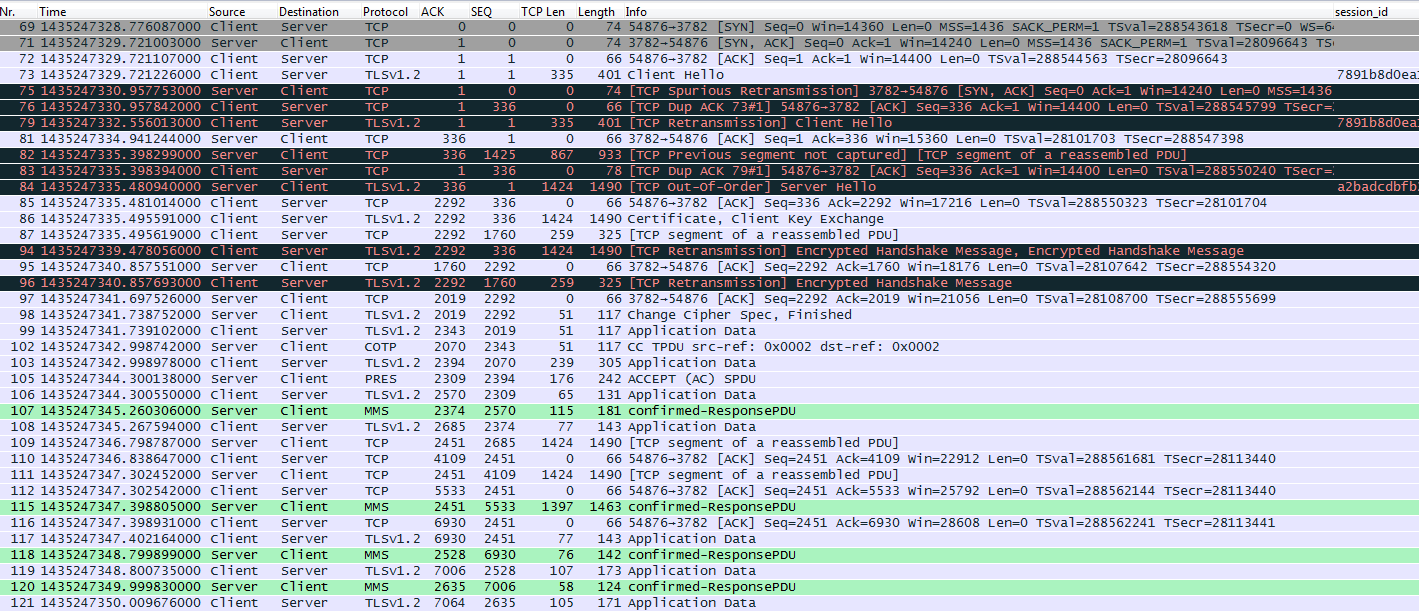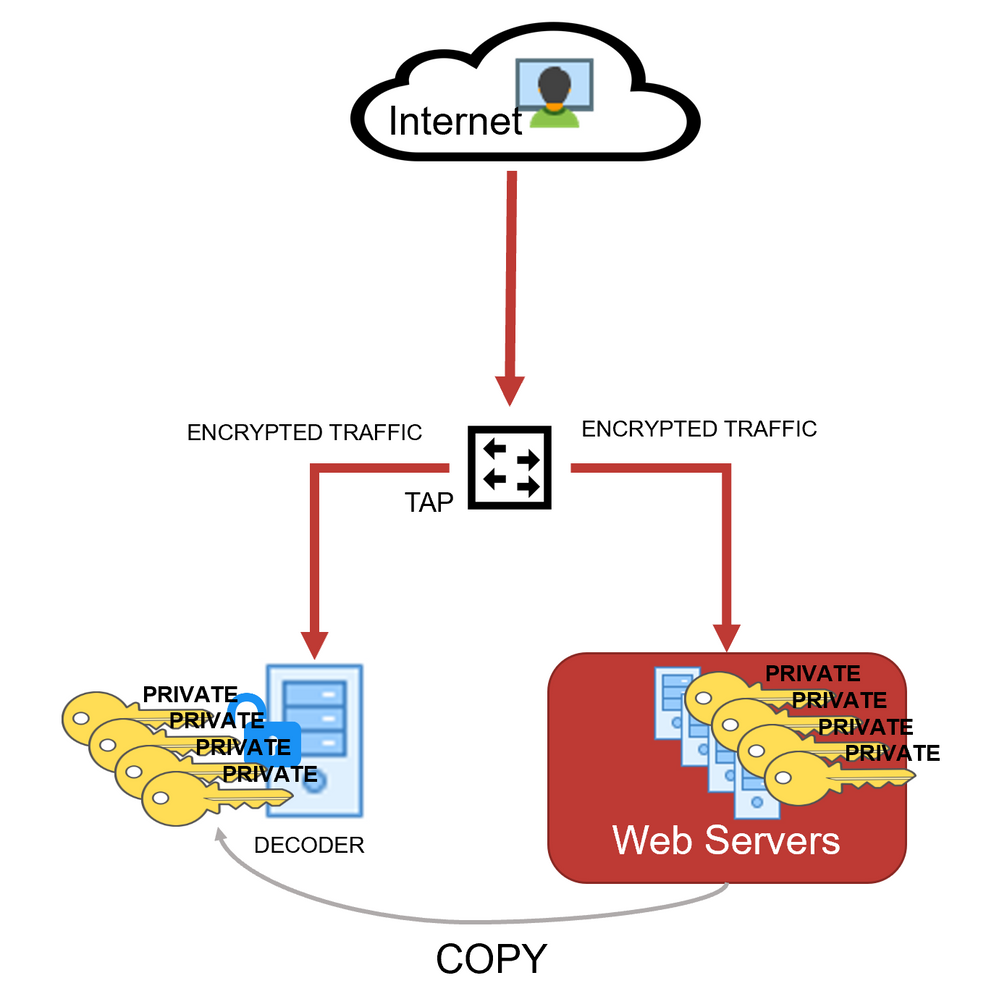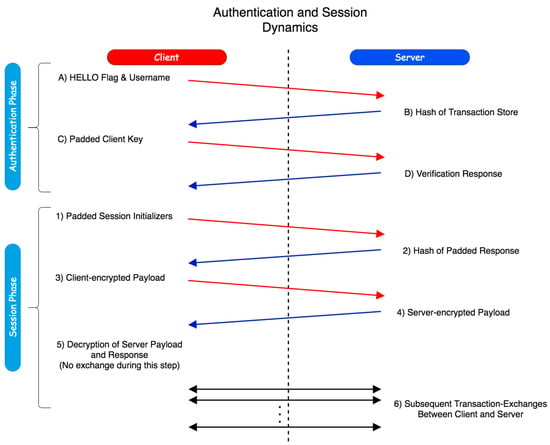
Sensors | Free Full-Text | A Hybrid Dynamic Encryption Scheme for Multi-Factor Verification: A Novel Paradigm for Remote Authentication
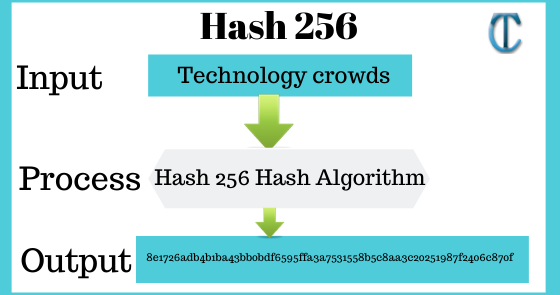
SHA 256: Compute a SHA 256 hash using C# for effective security - .Net Core | MVC | HTML Agility Pack | SQL | Technology Crowds

VESlocker: Hardware-grade PIN Security API - open source project - store PIN protected data in the browser's localStorage : r/webdev