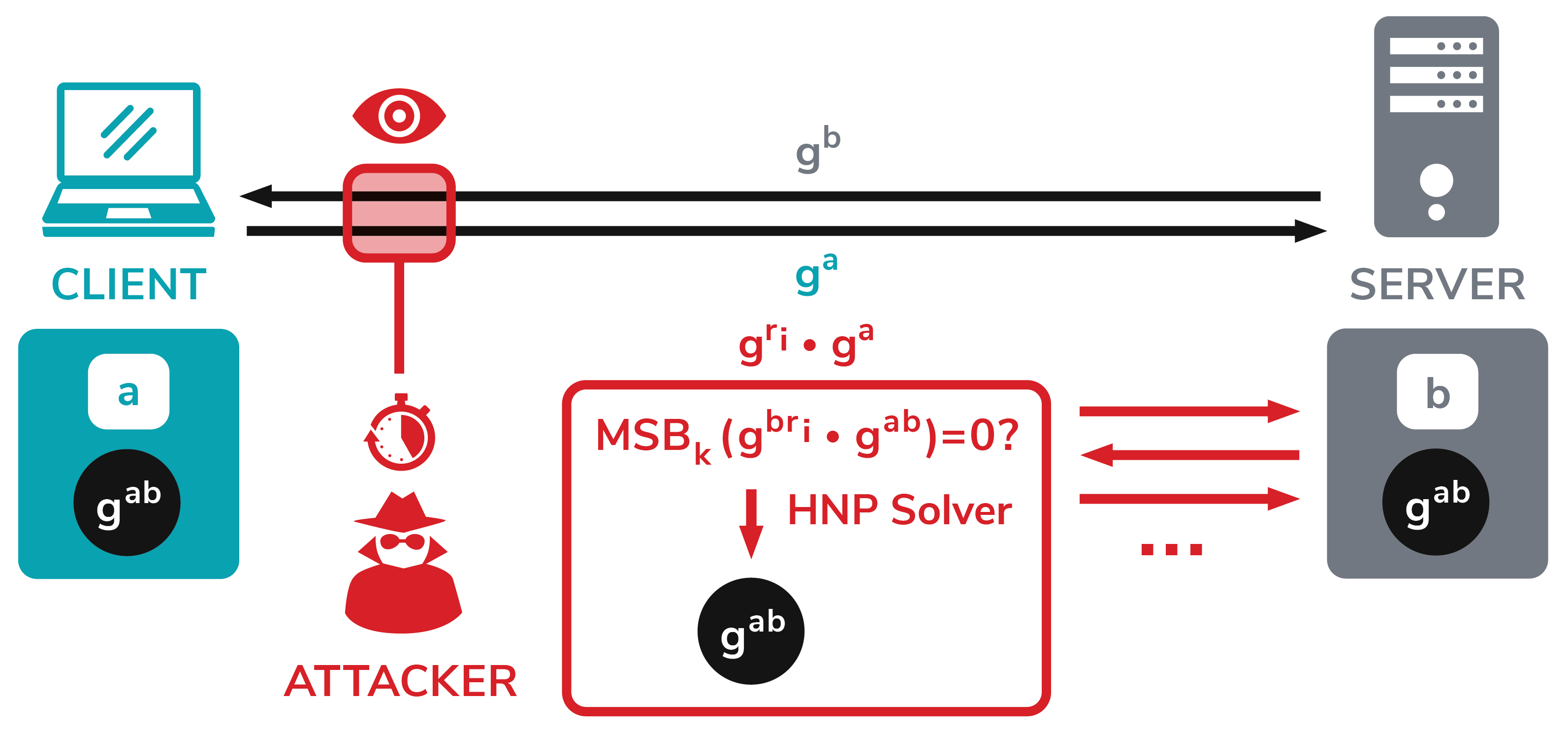
Vulnerability analysis of a ROS 2 robotic system. ROS: Robot Operating... | Download Scientific Diagram
Part of the kill chain': how can we control weaponised robots? | Artificial intelligence (AI) | The Guardian

Towards an open standard for assessing the severity of robot security vulnerabilities, the Robot Vulnerability Scoring System (RVSS) | DeepAI
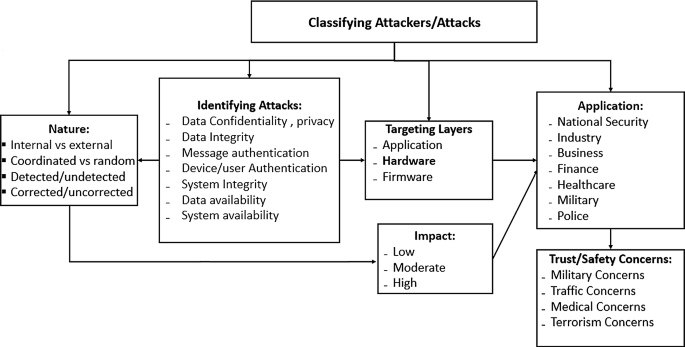
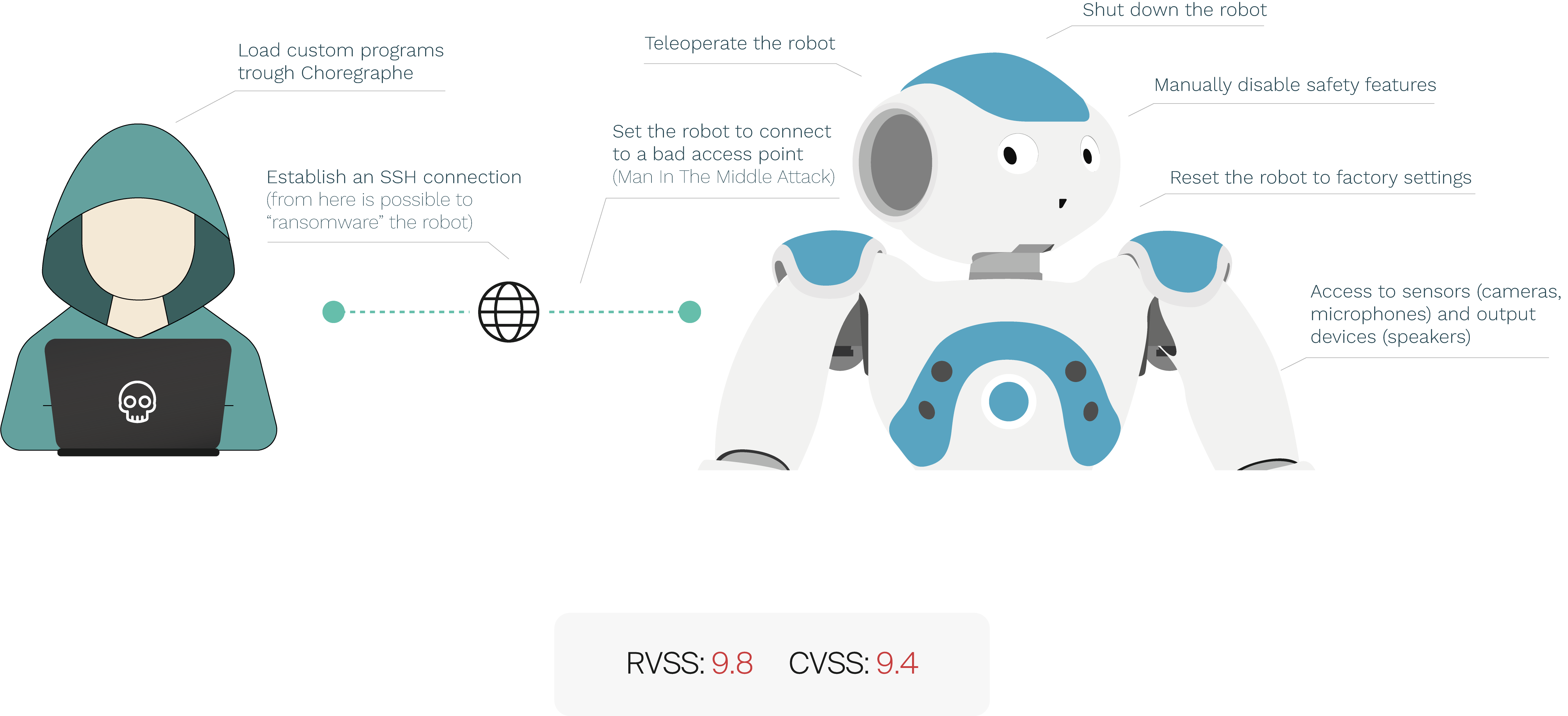
Robotics cyber security: vulnerabilities, attacks, countermeasures, and recommendations | SpringerLink