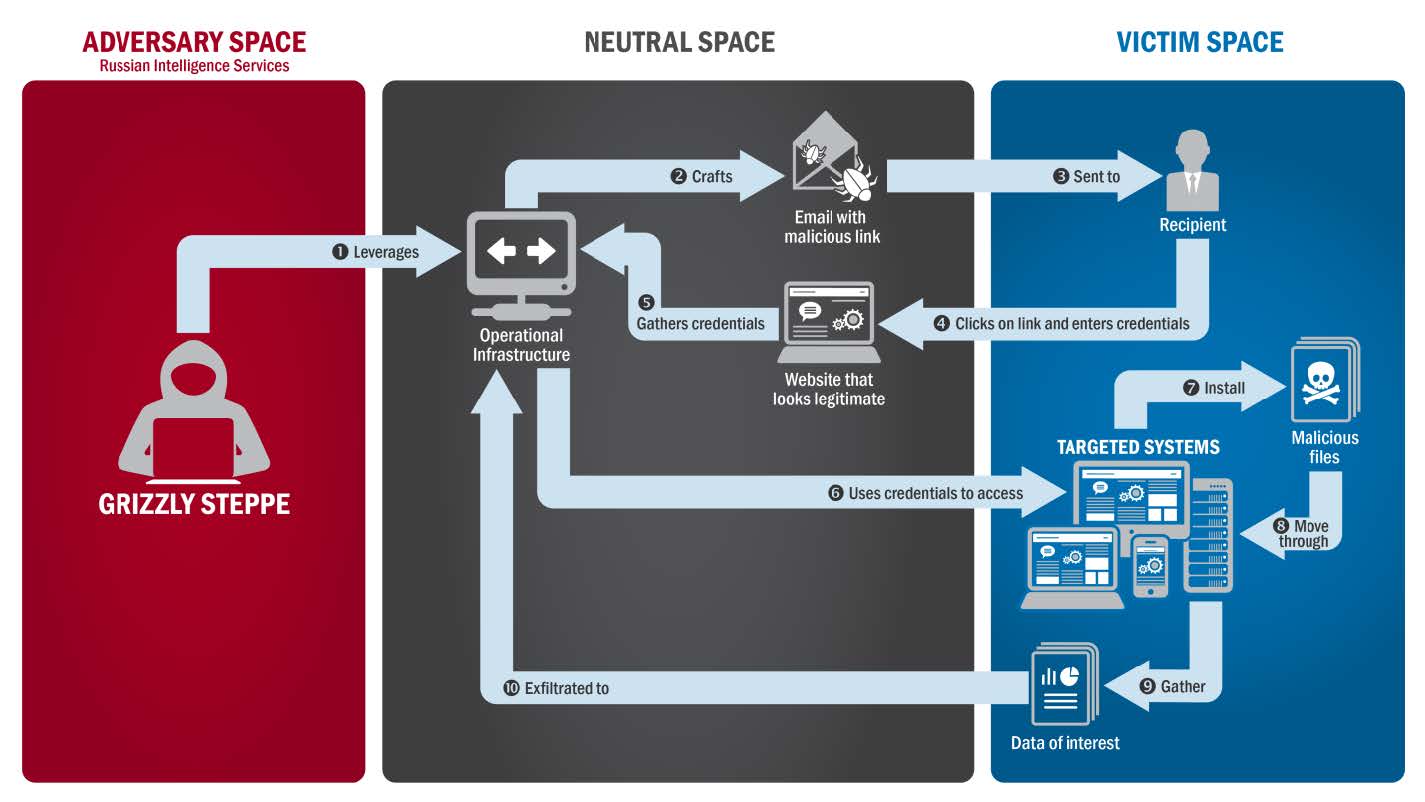
Executive Summary of Grizzly Steppe Findings from Homeland Security Assistant Secretary for Public Affairs Todd Breasseale | Homeland Security
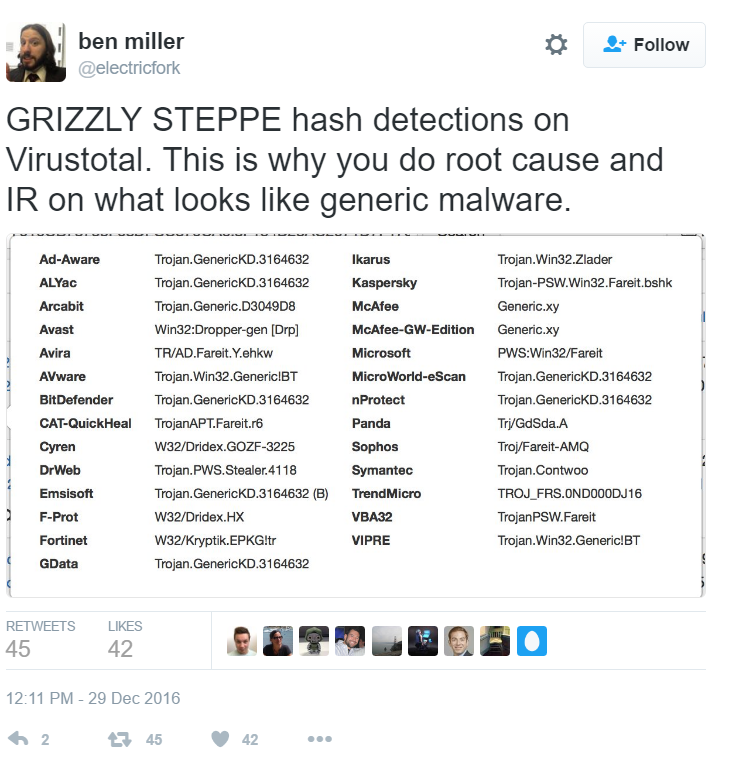
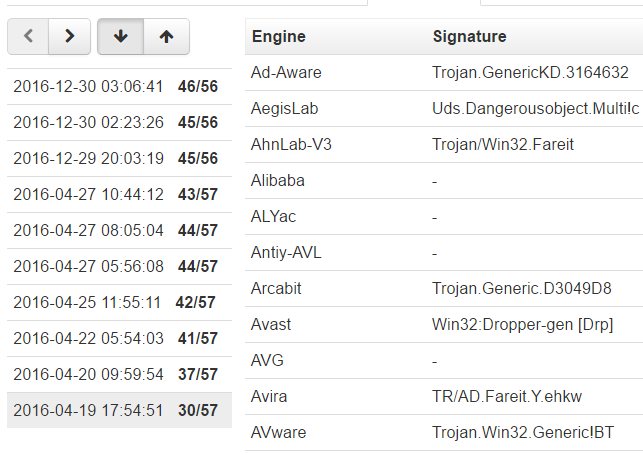
SANS Digital Forensics and Incident Response Blog | Critiques of the DHS/FBI's GRIZZLY STEPPE Report | SANS Institute

Russian Cyber Activity – The Grizzly Steppe Report by U.S. Department of Homeland Security, Federal Bureau of Investigation - Ebook | Scribd

Executive Summary of Grizzly Steppe Findings from Homeland Security Assistant Secretary for Public Affairs Todd Breasseale | Homeland Security