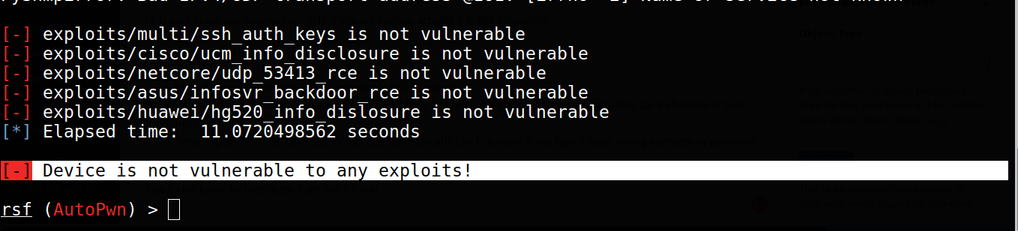
Cybersecurity Insights-7 - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.
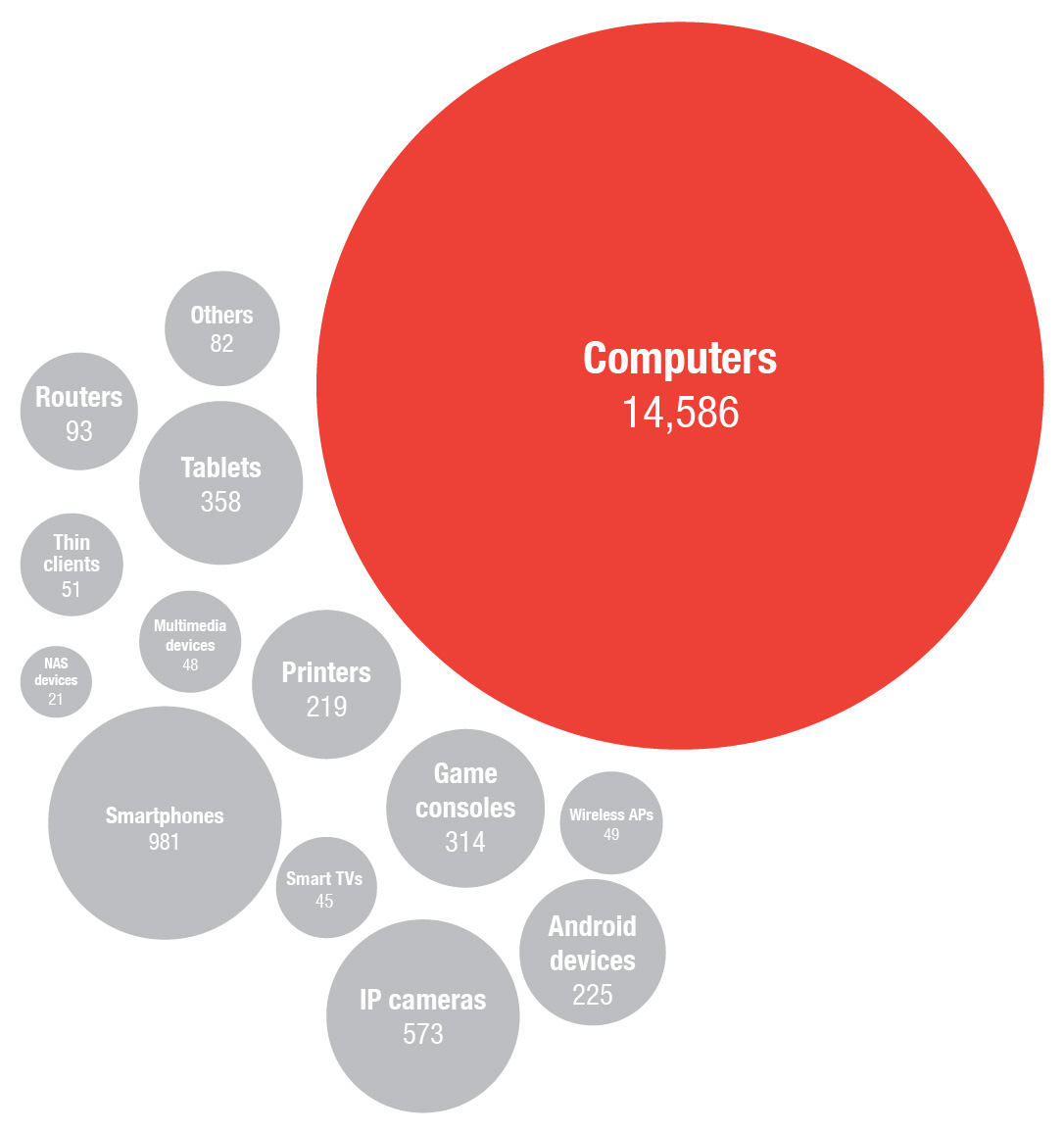
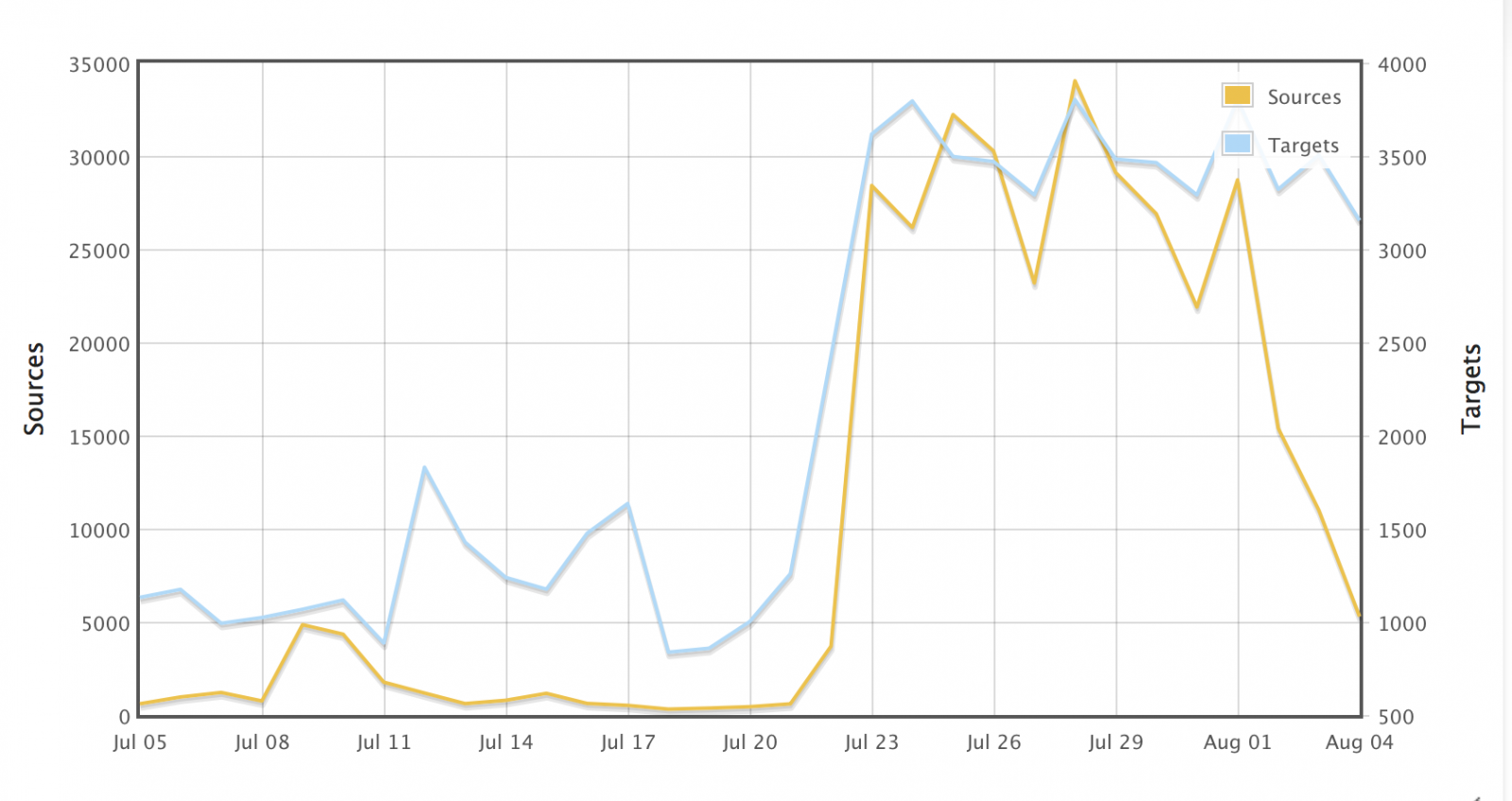
A Look Into the Most Noteworthy Home Network Security Threats of 2017 - Security Roundup - Trend Micro HK


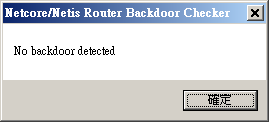
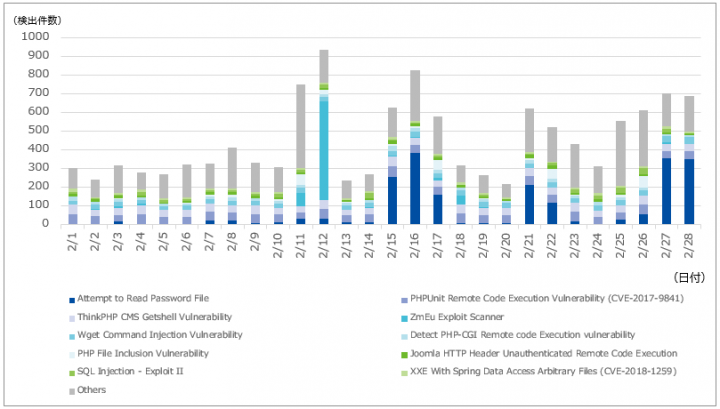

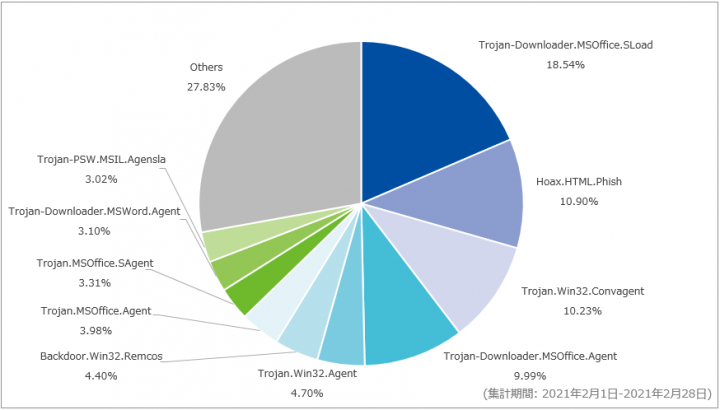







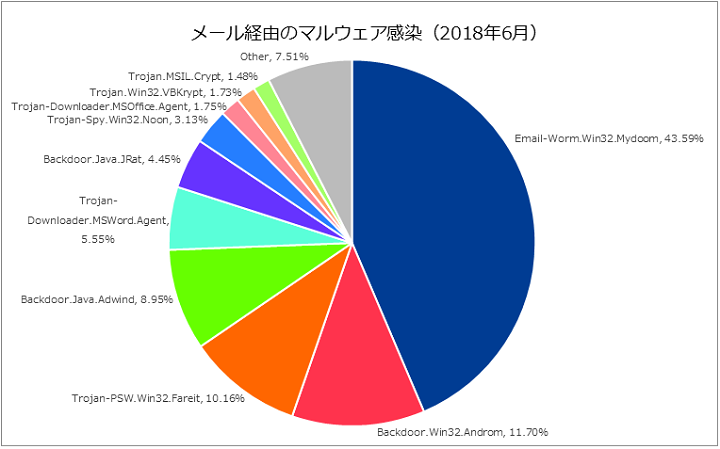


![Exploit a Router Using RouterSploit [Tutorial] - YouTube Exploit a Router Using RouterSploit [Tutorial] - YouTube](https://i.ytimg.com/vi/u0YrWfze9es/maxresdefault.jpg)